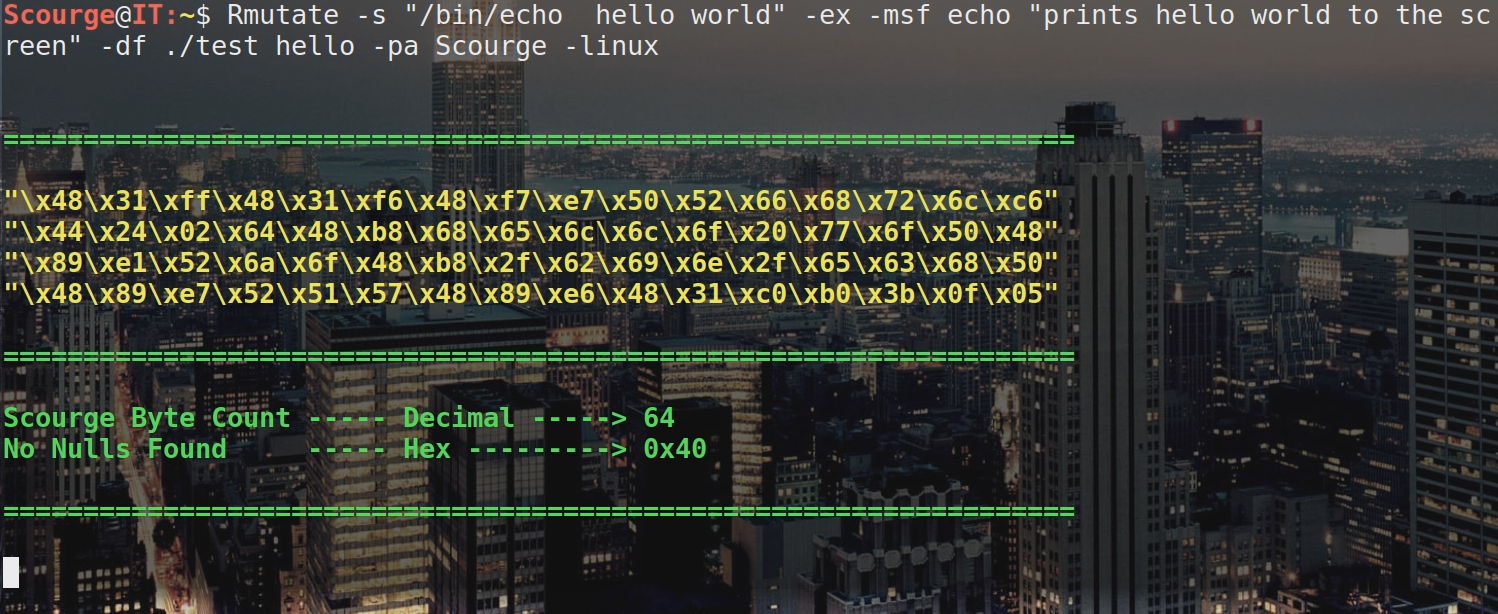
Here you will see how easy it is to instantly send your payloads to metasploit.
Even if you made a windows payload made with Rmutate.exe, you can still move that ruby file over to your other VM via a shared folder (which both VMware and VirtualBox have) and then have Rmutate send it to your MSF Framework.
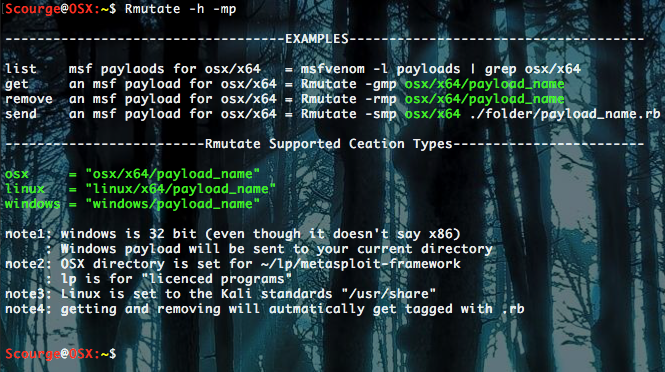
First, to create an msf payload, just use the “-msf” option with any metasploit command.
Next we will use grep to verify its existence.

Important note: The video below is out-dated
- Because I don’t pipe into Rmutate after using an msf encoder to auto-execute. To do this now, use the -bc (bytecode) and it will use that to execute from.
- Also because MSF’s x64/xor is VERY bad. For starters, because it uses xor.rb and not XorAdditiveFeedback.rb as the superclass. Secondly, because the shellcode is not polymorphic. I will re-do the video after illScrappy is released, the up-and-coming MSF Polymorphic Encoder.